杂记(1)
记录近期做的一些题,包括强网青少赛线下赛,NCTF,强网杯,楚慧杯,强网拟态决赛的部分赛题。
由于备战期末考,时间比较紧迫,以下分析中若有不足,请师傅们指点指点◝(⑅•ᴗ•⑅)◜
强网青少赛——未解之谜
task
1 | from Crypto.Util.number import getPrime, getRandomRange, inverse, bytes_to_long |
关键在
1 | d = phi - getRandomRange(2, int(root(n, 4))) // 8 |
设$x = $getRandomRange(2, int(root(n, 4))) // 8
$\because ed \equiv 1 \mod \phi(n)$,而且$d = \phi(n) - x$
即$e\phi(n) + e(-x) \equiv e(-x) \equiv 1 \mod \phi(n)$
$\therefore ex \equiv -1 \mod \phi(n)$
$ex = k\phi(n) - 1$
$\frac{e}{\phi(n)} = \frac{k}{x} - \frac{1}{x\phi(n)}$
$\frac{e}{n}\approx \frac{k}{x}$
$\because |\frac{e}{n}-\frac{k}{x}| \approx\frac{1}{n} < \frac{1}{2x^2}$
其中$n$是2048bit量级,而$x$是509bit量级,因此上式成立,即符合勒让德理论,因此可以连分数展开求d
需要注意的是,我们求的是$x$,但实际解密需要用$-x$解
exp:
1 | # sage |
NCTF
Signin
1 | # Sage |
output
1 | fx = [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, -1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, -1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, -1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1] |
题目实现了标准的NTRU密码系统,参考:NTRU密码系统 - 知乎 (zhihu.com)
该给的参数都给了
对照这文章的解密流程即可恢复
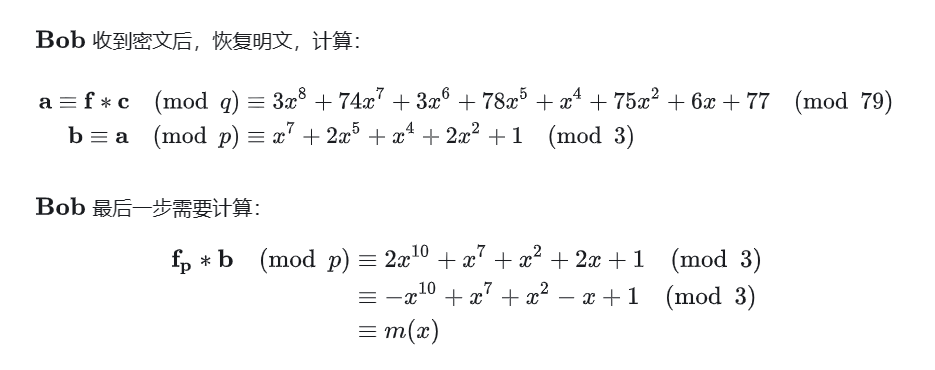
需要注意的是**计算$b\equiv a$的时候,要保证系数在$(\frac{-q}{2},\frac{q}{2})$**中
exp:
1 | #sage |
Code Infinite
首先声明这道题,由于前置知识不够扎实,导致我的理解其实很不充分,后面有时间会重新梳理思路。
util
1 | from hashlib import sha256 |
task
1 | #!/usr/local/bin/python |
简单来说,util中实现了椭圆曲线上的加法和乘法,还有一个验证
task中,我们通过验证后,可以输入4次点(x,y),主要任务是恢复PK
本题思路参考:Crypto趣题-曲线 | 糖醋小鸡块的blog (tangcuxiaojikuai.xyz)————————ECDH
大概是因为服务器没有对输入的点进行验证是否在曲线上,因此,我们可以改变参数b,构造一个曲线$y^2 \equiv x^3 +ax +b’$
下面具体的思路没有理清
大概就是利用CRT,用四次机会,输入四次我们曲线上的点$G_i$,服务器返回$G_i$的倍点$Q_i = PK\times G_i$
然后我们分别解4次$k_iG_i = Q_i$,最后对4个$k_i$求解CRT,即可恢复PK
因为服务器的曲线参数不变,于是我先连了4次靶机,来获得4个点,恢复出参数
如下
1 | from Crypto.Util.number import GCD,isPrime |
获得参数,发现$p \approx 192bit$,所以$PK \approx 192bit$
然后改变b,使得椭圆曲线的阶存在一些小因子
1 | a= 6277101735386680763835789423207666416083908700390324961276 |
需要注意的是,因为只有4次交互机会,所以我们每次解的$k_i$应该在50bit左右,这就要求小因子的乘积应该在50bit左右
如下,我选择的b使得曲线能有这样的小因子,这样既保证了求解$k_iG_i = Q_i$比较快(因为这样的阶很光滑)
1 | b = 11,a = 2**4*5*7706591*10310351 # 53bit |
最后exp:
1 | #sage |
赣CTF
Paillier
1 | from Crypto.Util.number import getStrongPrime,GCD,bytes_to_long |
网上找了个脚本,留个坑,将来有时间复现
exp:
1 | from Crypto.Util.number import * |
强网杯
被学长带飞了,排名58!!!
Vanish的wp👉2023 强网杯 初赛 (qq.com)
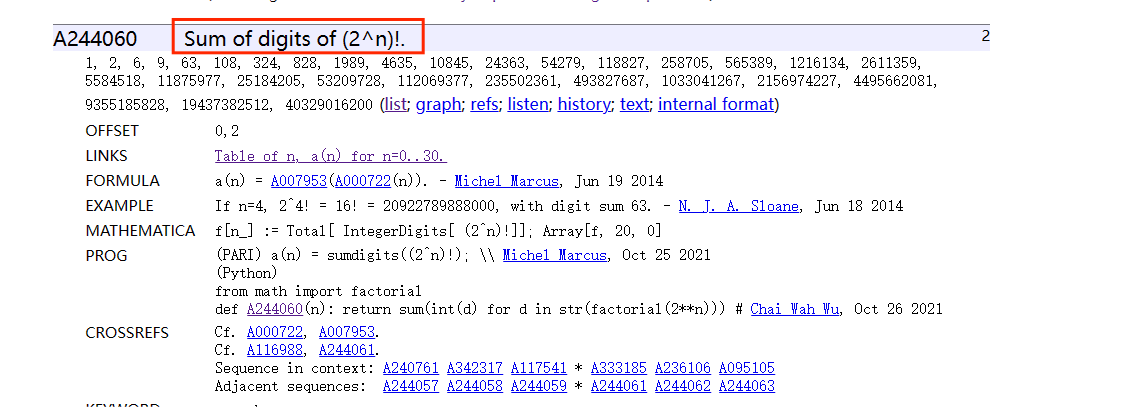
speed up
计算$2^{27}!$
task
1 | def f(x): |
f函数是把每个十进制位的值进行求和
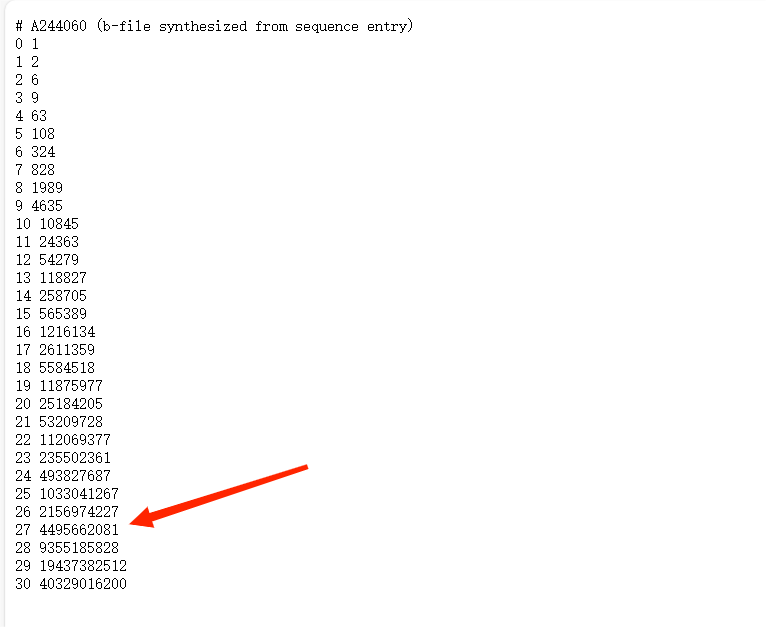
解法1
网站上找特殊的值
解法2
用Mathematica工具
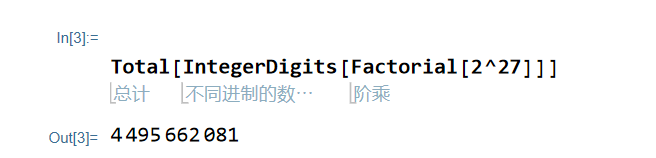
大概7分钟出结果
工具安装教程:Mathematica安装激活极简教程 - 知乎 (zhihu.com)
exp:
1 | import hashlib |
not only rsa
task
1 | from Crypto.Util.number import bytes_to_long |
out
1 | n = 6249734963373034215610144758924910630356277447014258270888329547267471837899275103421406467763122499270790512099702898939814547982931674247240623063334781529511973585977522269522704997379194673181703247780179146749499072297334876619475914747479522310651303344623434565831770309615574478274456549054332451773452773119453059618433160299319070430295124113199473337940505806777950838270849 |
n网站分解,拿到p
发现gcd(e,phi)=e
用sagemath自带的nth_root()
1 | #sage |
根据sagemath密码学 - vconlln - 博客园 (cnblogs.com)提到的
Zmod(n)(c).nth_root(t,all='True')作用是:在模$n$下求$c$的t次根
还可以求解离散对数
1 | x=mod(5,41) |
楚慧杯
so large e
task
1 | from Crypto.Util.number import * |
提取公钥得到n,e
发现$\frac{d}{n} = 0.26269$
多半就是boneh_durfee攻击手段
改改example()函数的delta和m即可
delta就是$\frac{d}{n}$的大小
exp:
1 | #sage |
解的d = 663822343397699728953336968317794118491145998032244266550694156830036498673227937
最后解RSA
flag:DASCTF{6f4fadce-5378-d17f-3c2d-2e064db4af19}
强网拟态决赛
BadRSA
1 | from Crypto.Util.number import * |
由$ed \equiv 1 \mod \phi(n)$
即$ed = k(p-1)(q-1) + 1$
两边同时模$2^{265}$,得$ed_0 \equiv k(p-1)(q-1) + 1 \mod 2^{265}$,这里$d_0 = leak$
$\therefore ed_0 \equiv k(pq - p - q + 1) + 1 \mod 2^{265}$
再同乘$p$,得到$ed_0p \equiv knp - kp^2 - kn + kp + p \mod 2^{265}$
因为$d \approx 1023bit$
所以$k < e$
爆破$k$,解方程得到$p$的低位,然后用copper恢复$p$
exp:
1 | from Crypto.Util.number import * |
这里beta = 0.5是因为,对于度(即最大次方)为$d$的多项式,要求根小于$n^{\frac{\beta^2}{d} - \epsilon}$,而且要求因子$p > n^{\beta}$
此题$d = 1$,经过计算我们要求的根的上界为$2^{247}$,$\frac{247}{1024} = 0.2412$,所以取beta = 0.5可以恢复p