2024HGAME
记录2024HGAME网络攻防大赛Crypto题解
仅分享本人的做法,并非正解
Week1
ezMath
task.py
1 | from Crypto.Util.number import * |
解佩尔方程得到y
exp
1 | # sage |
ezRSA
task.py
1 | from Crypto.Util.number import * |
已知
$$
leak_1 \equiv p^q \mod n
$$
$$
leak_2 \equiv q^p \mod n
$$
两个式子相乘即可得到:$leak_1 \times leak_2 \equiv p^q \times (q^q \times q^{p-q}) \mod n$
即:$leak_1 \times leak_2 \equiv n^{q} \times q^{p-q} \equiv 0 \mod n$
所以$leak_1 \times leak_2 = kn$
从 $leak_1 \equiv p^{q} \mod n$可以推出 $leak_1 \equiv p^q \equiv p \mod q$
同理 $leak_2 \equiv q^p\mod n$可以推出 $leak_2 \equiv q^p \equiv q \mod p$
通过解下面这个方程即可得到p,q
$$
leak_1 + leak_2 = p + q\
kn = p \times q
$$
Exp
1 | from Crypto.Util.number import * |
ezPRNG
task.py
1 | from Crypto.Util.number import * |
类似2018CISCN-old Streamgame
分析代码
PRNG函数的作用是产生新的R
产生方式:
假设初始的R如下

把R的低32位作为一个整体如$R_1$,把这个整体和mask进行与操作,存为
i然后左移一位,此时R变成

然后把R从最低位,到最高位依次亦或,把最后的值记为
nextbit把
nextbit作为R的最低位,此时R的值变为这样

自始至终R都是32位
因为nextbit是和i的每一位亦或而来,所以当i中有偶数个1的时候,nextbit的值为0,当i中有奇数个1的时候,nextbit的值为1
又因为i = (R & mask) & 0xffffffff,mask = 0b10001001000010000100010010001001 ,mask中第1,4,8,11,15,20,25,28,32位是1,再结合&操作的性质,我们可以推断出,nextbit的值,取决于R中第1,4,8,11,15,20,25,28,32位的值
也就可以写出表达式
nextbit = $R_1 \otimes R_4 \otimes R_8 \otimes R_{11} \otimes R_{15} \otimes R_{20} \otimes R_{25} \otimes R_{28} \otimes R_{32}$
$\therefore R_{32} = R_1 \otimes R_4 \otimes R_8 \otimes R_{11} \otimes R_{15} \otimes R_{20} \otimes R_{25} \otimes R_{28} \otimes nextbit$
根据这个状态

我们就能求$R_{32}$
再根据下一个状态,就是R30 ... R1 nextbit1 nextbit2这个状态,我们就能求$R_{31}$
以此类推即可恢复R
虽然题目给出了1000个状态,我们只需要用上前32个状态
exp
1 | output=['1111110110111011110000101011010001000111111001111110100101000011110111111100010000111110110111100001001000101101011110111100010010100000011111101101110101011010111000000011110000100011101111011011000100101100110100101110001010001101101110000010001000111100101010010110110111101110011011001011111011010101011000011011000111011011111001101010111100101100110001011010010101110011101001100111000011110111000001101110000001111100000100000101111100010110111001110011010000011011110110011000001101011111111010110011010111010101001000010011110110011110110101011110111010011010010110111111010011101000110101111101111000110011111110010110000100100100101101010101110010101001101010101011110111010011101110000100101111010110101111110001111111110010000000001110011100100001011111110100111011000101001101001110010010001100011000001101000111010010000101101111101011000000101000001110001011001010010001000011000000100010010010010111010011111111011100100100100101111111001110000111110110001111001111100101001001100010', '0010000000001010111100001100011101111101111000100100111010101110010110011001011110101100011101010000001100000110000000011000000110101111111011100100110111011010000100011111000111001000101001110010110010001000110010101011110011101000011111101101011000011110001101011111000110111000011000110011100100101100111100000100100101111001011101110001011011111111011010100010111011000010010101110110100000110100000100010101000010111101001000011000000000111010010101010111101101011111011001000101000100011001100101010110110001010010001010110111011011111101011100111001101111111111010011101111010010011110011111110100110011111110110001000111100010111000101111000011011011111101110101110100111000011100001010110111100011001011010011010111000110101100110100011101101011101000111011000100110110001100110101010110010011011110000111110100111101110000100010000111100010111000010000010001111110110100001000110110100100110110010110111010011111101011110000011101010100110101011110000110101110111011010110110000010000110001', '1110110110010001011100111110111110111001111101010011001111100100001000111001101011010100010111110101110101111010111100101100010011001001011101000101011000110111000010000101001000100111010110001010000111110110111000011001100010001101000010001111111100000101111000100101000000001001001001101110000100111001110001001011010111111010111101101101001110111010111110110011001000010001010100010010110110101011100000101111100100110011110001001001111100101111001111011011010111001001111010001100110001100001100000110000011111010100101111000000101011111010000111110000101111100010000010010111010110100101010101001111100101011100011001001011000101010101001101100010110000010001110011110011100111000110101010111010011010000001100001011000011101101000000011111000101111101011110011000011011000100100110111010011001111101100101100011000101001110101111001000010110010111101110110010101101000000101001011000000001110001110000100000001001111100011010011000000011011101111101001111110001011101100000010001001010011000001', '0001101010101010100001001001100010000101010100001010001000100011101100110001001100001001110000110100010101111010110111001101011011101110000011001000100100101000011011101000111001001010011100010001010110111011100100111110111001010010111010100000100111110101110010010110100001000010010001101111001110100010001011101100111011101011101100100101011010101000101001000101110011011111110110011111111100000000011100000010011000110001000110101010001011000010101000110000101001110101010111011010010111011001010011100010101001100110000110101100010000100110101110100001101001011011110011100110011001010110100101010111110110111100000111010001111101110000000000111011011101000011001010010111001110111000100111011110100101000100011011101100011111000101110110110111111001111000000011100011000010000101001011001101110101000010101001000100110010000101001111100101000001011011010011110001101000001101111010100101001100010100000111000011110101010100011011001110001011110111010111011010101101100000110000001010010101111011'] |
Week2
MidRSA
task.py
1 | from Crypto.Util.number import * |
考点:m高位泄露
exp
1 | #sage |
MidRSA revenge
task.py
1 | from Crypto.Util.number import * |
exp
1 | from Crypto.Util.number import long_to_bytes |
backpack
task.py
1 | from Crypto.Util.number import * |
背包密码一把梭,👉背包密码 | DexterJie’Blog
因为p移位之后才与flag亦或,移位后的p只有12bit,对flag的影响很小,所以可以直接long_to_bytes(enc)得到flag的大部分信息
exp
1 | #sage |
backpack revenge
task.py
1 | from Crypto.Util.number import * |
普通的LLL规约出的结果并不好,换用BKZ
block_size越大,效果越好,运行越慢
exp
1 | import libnum |
babyRSA
task.py
1 | from Crypto.Util.number import * |
$$
gift \equiv (e + 114514 + p^k)^{65537} \mod p
$$
$$
\therefore gift \equiv (e + 114514)^{65537} \mod p
$$
解一次RSA得到$e$
发现e和$\phi(n) = p^3(p-1)(q-1)$不互素
用nthroot处理
exp
1 | # sage |
Week3
exRSA
task.py
1 | from Crypto.Util.number import * |
3对ed,扩展维纳攻击
exp
1 | import gmpy2 |
matrix_equation
task.py
1 | from Crypto.Util.number import * |
构造格
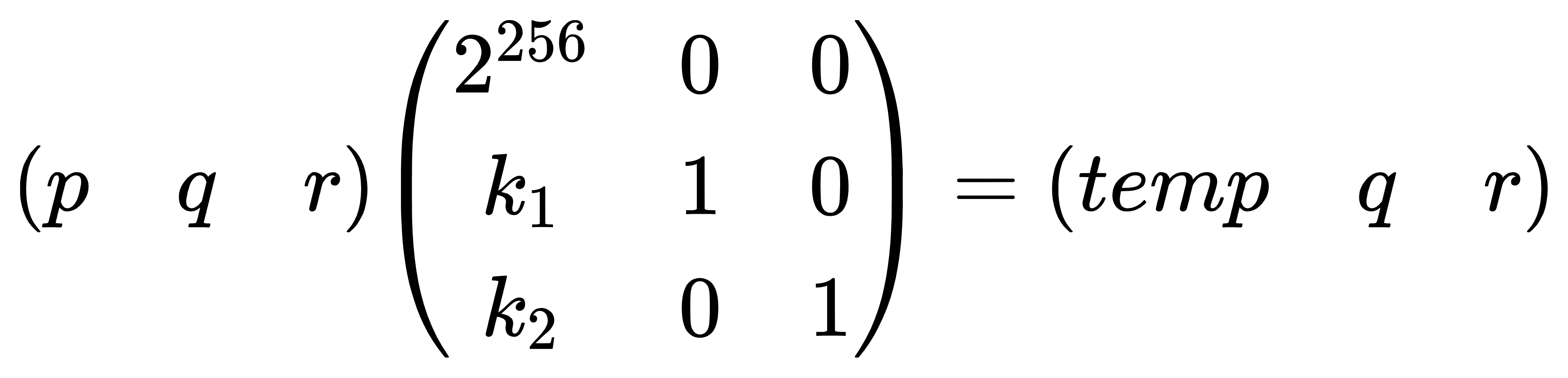
因为$temp \approx 2^{83}$,不需要调整格的大小
HNP
task.py
1 | from Crypto.Util.number import * |
根据题意有
$$
enc_i \equiv t_i \times m \mod p
$$
且$res_i \equiv enc_i \mod (2^{32} + 1)$
记$enc_i$的高位为$R_{ihigh}$,$res_i$为$r_i$
所以有
$$
R_{ihigh}\times (2^{32} + 1) + r_i \equiv t_i \times m \mod p
$$
把$R_{ihigh}$单独放左边有
$$
R_{ihigh} \equiv (t_i \times m -r_i) \times (2^{32}+1)^{-1} \mod p
$$
即
$$
R_{ihigh} = (t_i\times m - r_i)\times (2^{32}+1)^{-1} +k_i \times p
$$
即inv = $(2^{32} + 1)^{-1}$
构造格
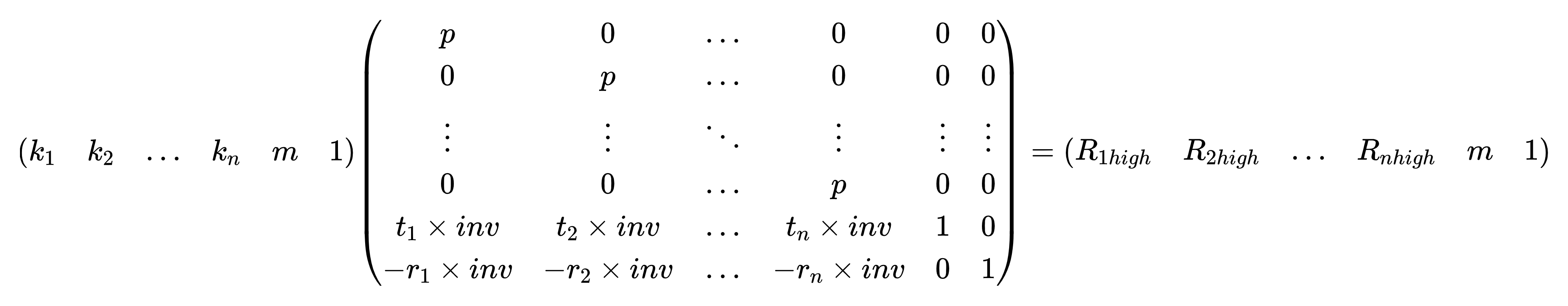
根据$p = 512bit$,推出$m = 504bit$,$R_{ihigh} = 480bit$
调整格为
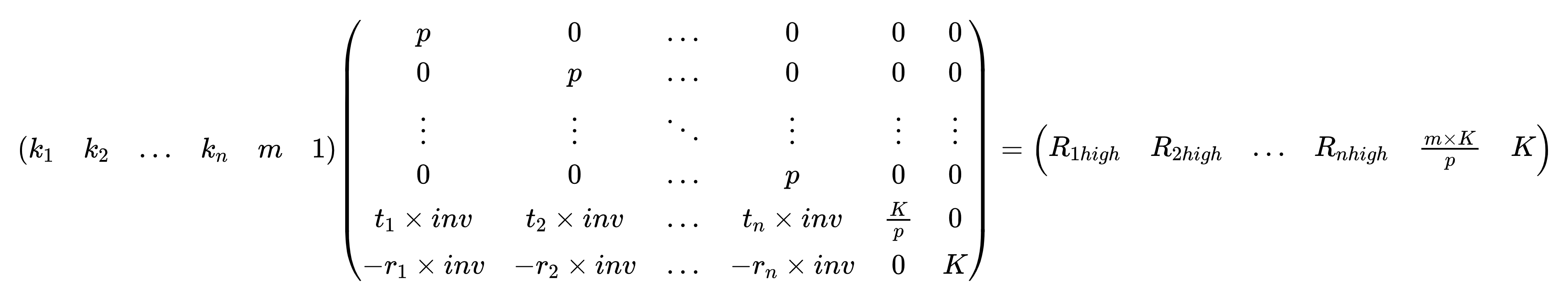
其中$K = 2^{480}$
exp:
1 | from Crypto.Util.number import * |
Week4
lastRSA
task.py
1 | from Crypto.Util.number import * |
先求leak,再剪枝。这里剪枝的代码参考DASCTF七月赛
求leak用到了富兰克林相关消息攻击+HGCD
exp
1 | from Crypto.Util.number import long_to_bytes |
看flag的意思应该要用gb基来完成
transformation
task.py
1 | #!/usr/bin/env python |
参考SICTF的那道题
先恢复扭曲爱德华曲线的参数
1 | import gmpy2 |
这题不同之处在于要乘上$e^{-1} \mod order$来恢复在weis的G点,再映射回爱德华曲线
Exp
1 | #sage |