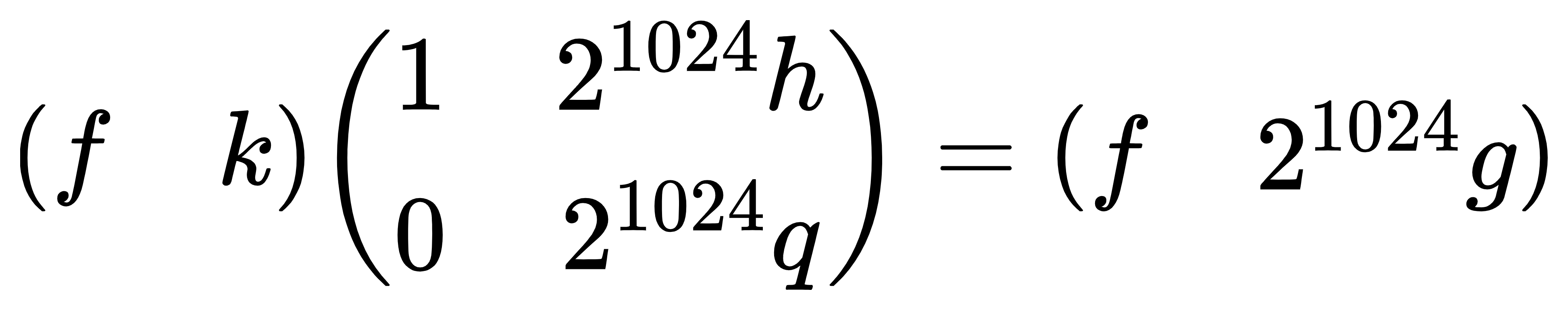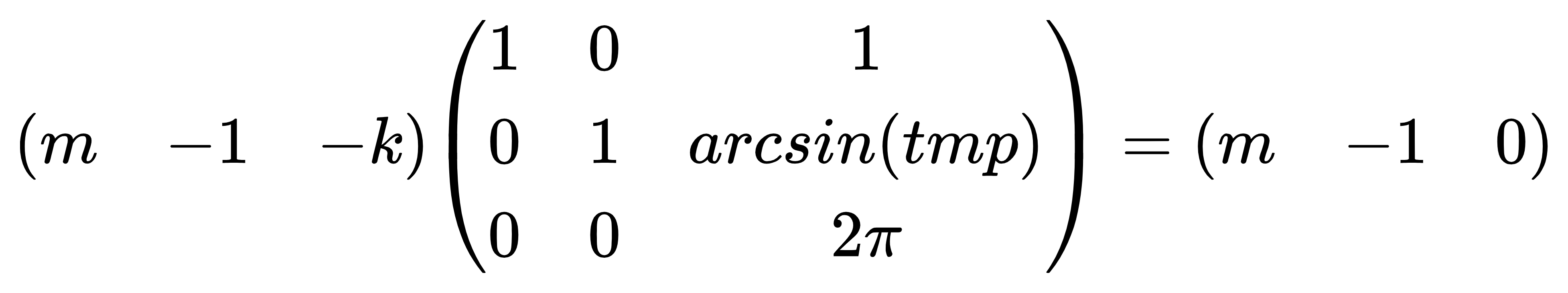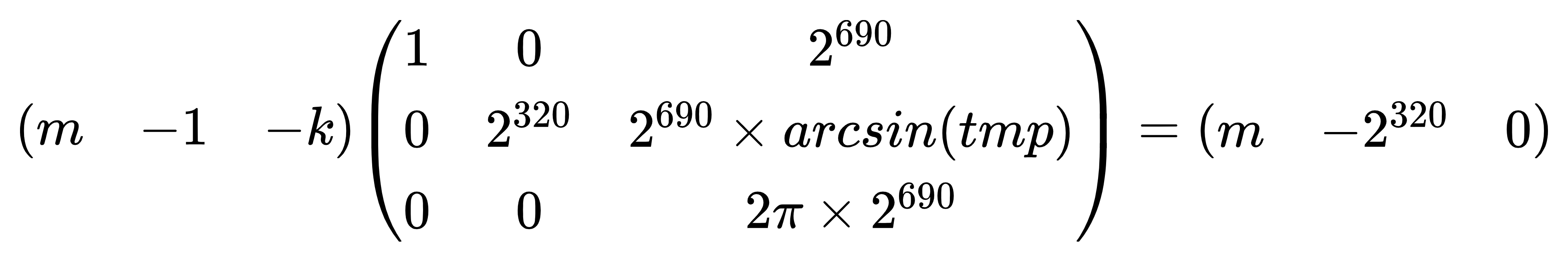1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
|
from random import sample
from os import urandom
from secret import flag
from binascii import unhexlify
logo = '''
.---. ,--, ____
/. ./| ,--.'| ,' , `.
.--'. ' ; | | : ,---. ,-+-,.' _ |
/__./ \ : | : : ' ' ,'\ ,-+-. ; , ||
.--'. ' \' . ,---. | ' | ,---. / / | ,--.'|' | || ,---.
/___/ \ | ' ' / \ ' | | / \ . ; ,. : | | ,', | |, / \
; \ \; : / / | | | : / / ' ' | |: : | | / | |--' / / |
\ ; ` | . ' / | ' : |__ . ' / ' | .; : | : | | , . ' / |
. \ .\ ; ' ; /| | | '.'| ' ; :__ | : | | : | |/ ' ; /|
\ \ ' \ | ' | / | ; : ; ' | '.'| \ \ / | | |`-' ' | / |
: ' |--" | : | | , / | : : `----' | ;/ | : |
\ \ ; \ \ / ---`-' \ \ / '---' \ \ /
'---" `----' `----' `----'
___
,--.'|_
| | :,' ,---.
: : ' : ' ,'\
.;__,' / / / |
| | | . ; ,. :
:__,'| : ' | |: :
' : |__ ' | .; :
| | '.'| | : |
; : ; \ \ /
| , / `----'
---`-' ____
,' , `. ,---, ,---,. ,---,
,-+-,.' _ | .' .' `\ ,' .' | ' .' \
,-+-. ; , || ,--, ,---.' \ ,---.' | / ; '.
,--.'|' | ;| ,'_ /| | | .`\ | | | .' : : \
| | ,', | ': .--. | | : : : | ' | : : : : | /\ \
| | / | | || ,'_ /| : . | | ' ' ; : : | |-, | : ' ;. :
' | : | : |, | ' | | . . ' | ; . | | : ;/| | | ;/ \ \
; . | ; |--' | | ' | | | | | : | ' | | .' ' : | \ \ ,'
| : | | , : | : ; ; | ___ ' : | / ; ' : ' | | ' '--'
| : ' |/ ' : `--' \ .' .`| | | '` ,/ | | | | : :
; | |`-' : , .-./ .' .' : ; : .' | : \ | | ,'
| ;/ `--`----' ,---, ' .' | ,.' | | ,' `--''
'---' ; | .' '---' `----'
`---'
'''
_memu = '''
1. Encrypt
2. Get flag
3. Exit
'''
def rotl(x, n): return ((x << n) & 0xffffffff) | ((x >> (32 - n)) & 0xffffffff)
def xorl(x, y): return list(map(lambda a, b: a ^ b, x, y))
def i2l(x): return [x >> 24, (x >> 16) & 0xff, (x >> 8) & 0xff, x & 0xff]
def l2i(x): return x[0] << 24 | x[1] << 16 | x[2] << 8 | x[3]
class Enc:
def __init__(self, key: bytes):
self.K = key
self.S = sample([i for i in range(256)], 256)
def l(self, B: list) -> list:
B = l2i(B)
B = B ^ rotl(B, 2) ^ rotl(B, 10) ^ rotl(B, 18) ^ rotl(B, 24)
return i2l(B)
def encrypt(self, plain: bytes) -> bytes:
T = xorl(self.K[:4], plain)
T = self.l([self.S[i] for i in T])
T = xorl(self.K[4:], T)
return bytes(T).hex()
def E():
plain = input("plz enter your plaintext: ")
if len(plain) != 8:
print("wrong length")
exit(0)
print(C.encrypt(unhexlify(plain)))
def get_flag():
print(f"cipher is {f}")
plain = input("plz enter your plaintext: ")
if len(plain) != 8:
print("wrong length")
exit(0)
c = C.encrypt(unhexlify(plain))
if c == f:
print(flag)
exit(0)
else:
print("fake!")
exit(0)
def memu():
choose = input("> ")
if choose == "1":
E()
elif choose == "2":
get_flag()
else:
print("bye!~")
exit(0)
if __name__ == "__main__":
print(logo)
key = urandom(8)
C = Enc(key)
f = C.encrypt(urandom(4))
print(f"sbox: {C.S}")
print(_memu)
while True:
memu()
|