2024强网杯线下赛
记录2024S8强网杯线下赛Crypto部分题解和RealWorld部分题目信息,还有自我感受
比赛分为两个部分,一个是Jeopardy(就是平时的解题赛),另外一个是RW(RealWorld,和实战没什么区别,看了下题目基本都是现场挖洞,第一天拿分的基本都是长亭和DAS)
比赛记录
Jeopardy
解题部分就只记录密码,因为别的我也不会啊(楽)
Shopping
task.py
1 | from secret import flag |
$$
q = p + x
$$
$x \approx 2^{30}$
$$
n = pq = p(p + x)
$$
要求用+,-,%,//,*,iroot6个运算,进行有限步操作把n分解
$$
n = p^2 + px
$$
$$
n - px = p^2
$$
exp.py
1 | from pwn import * |
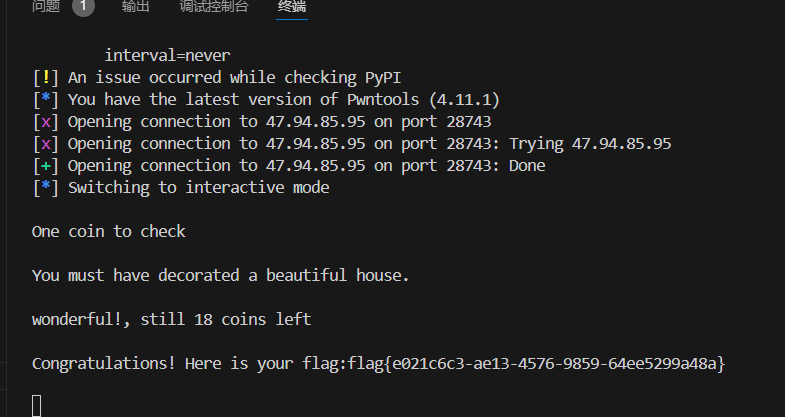
bl0ck
aes.py
1 | #!/usr/bin/env python3 |
server.py
1 | from aes import AES |
注意到第一轮结束时 state = E_k(block1)
最后要求state = b"\x00"*16,那么我们就构造一个block1 = D_k(b"\x00"*16)使得b"\x00"*16 = E_k(block1)
这里有个坑点是,他用的是block1加密key,而非用key加密block1。
构造的话,根据9轮AES去逆就好了。
exp.py
1 | #!/usr/bin/env python3 |
手动交互即可

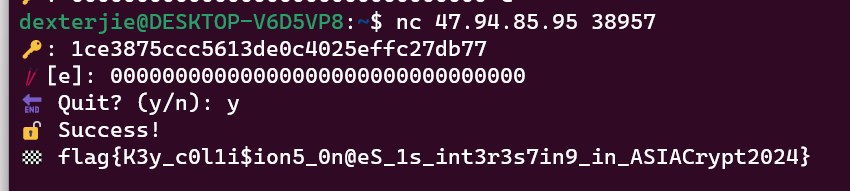
fak1
ntru.sage
1 | import random |
task.py
1 | from sage.all import * |
由加密可知
$$
C_i = pk \times r_i + m_i
$$
记$m_i = Secret + M_i$,$M_i$为用户输入的明文
取两组进行分析
$$
C_i = pk\times r_i + m_i
$$
$$
C_j = pk\times r_j + m_j
$$
两式相减
$$
C_i - C_j = pk(r_i - r_j) + (m_i + m_j)
$$
$$
\therefore C_i - C_j = pk(r_i - r_j) + (M_i - M_j)
$$
我们可以计算出$r_i - r_j$的值
$$
r_i - r_j = ((C_i - C_j) - (M_i - M_j))\times pk^{-1}
$$
$r_i,r_j$的系数为0,1。然后讨论$r_i - r_j$的值
1 | 当ri - rj = 0的时候,有可能为0-0,也有可能1-1 |
我们可以有9组这样的值,很大概率能够恢复$r_i$。恢复$r_i$之后通过$C_i = pk\times r_i + (Secret + M_i)$恢复Secret
测试了一下
1 | from Crypto.Util.number import * |
exp
1 | from Crypto.Util.number import * |
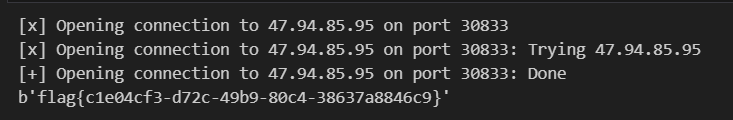
f2ke——unsolved
task.py
1 | from sage.all import * |
Signin——unsolved
task.py
1 | from hashlib import sha256 |
b1ock——unsolved
des.py
1 | import random |
server.py
1 | import os |
st——unsolved
这个,感觉就是个逆向,给了个data.bin和encrypt文件,要逆encrypt,然后data.bin寸的像是终端输入的信息,无果,连密码部分都没碰到。
RW
这部分更是一点都做不动。
压缩包密码
1 | klmT0%Gamo+g : rw_FXPDF.zip |
FXPDF
题目信息:
题目名称:FXPDF
旗帜名称:FXP
题目描述:附件中给出了一个已经正确安装Foxit PDF Editor Pro的Win10虚拟机,该虚拟机与台上靶机内的虚拟机环境完全相同,仅有系统密码不同。请挖掘并利用Foxit PDF Editor Pro中的漏洞,构造一个恶意PDF文档,实现在靶机的Win10 虚拟机中打开该文档后,能自动弹出系统计算器。上台演示的时候注意关闭exp的调试信息。
附件信息: 附件中的虚拟机与台上靶机内的虚拟机环境完全相同,仅有系统密码不同。附件中虚拟机系统用户名为jack,密码为admin。
台上拓扑:交换机同时连接选手攻击机和靶机。靶机中使用vmware(最新版)开启附件中提供的虚拟机环境(操作系统Win10,仅系统密码和附件中的虚拟机不同),该虚拟机中已经正确安装Foxit PDF Editor Pro。
展示目标:选手携带自己的攻击机上台,将可以完成漏洞利用的恶意PDF文档文件上传到自己的HTTP服务器。操作员将在靶机的Win10 虚拟机中,下载并打开选手HTTP服务器上的恶意PDF文档,该文档需要在打开后的规定的时间内,自动在Win10 虚拟机中弹出系统计算器。
DataEase
题目信息:
题目名称:DataEase
旗帜名称:D-E
题目描述:附件中给出了一个已经正确的DataEase环境,展台上仅开放81端口,请通过81端口进行攻击,并获取靶机权限,从而将https://ip:81/flag.html的页面修改为特定主页。账号密码均为dataease
附件信息:附件为台上相同(除密码不同)的环境,但开放端口不同,展台仅开放81端口。
台上拓扑:交换机同时连接选手攻击机和靶机。靶机中使用vmware(最新版)开启附件中的虚拟机环境(操作系统ubuntu,密码和附件不同),该虚拟机中部署了DataEase系统。虚拟机中仅有81端口被转发映射至靶机的81端口,可以使选手直接访问。且展台靶机允许回连选手机器
展示目标:选手携带自己的攻击机上台,需要在规定的时间内攻击81端口的服务程序,实现获取靶机权限,从而将主页的https://ip:81 /flag.html的页面修改为特定页面。需要修改的特定页面详见附件中的flag.html,选手展示时需将其替换为“hacked by ”,为自己的队伍名。
gnac
题目信息:
题目名称:gnac
旗帜名称:GNC
题目描述:题目给出了一台Genian NAC虚拟机,请选手攻击该镜像,修改admin用户密码,实现登录https://192.168.143.19:8443/mc2/faces/adminlogin.xhtml。
附件信息:附件为台上相同的攻击环境,但是密码不同。
台上拓扑:交换机同时连接选手攻击机和靶机。靶机中使用vmware(最新版)启动附件中的gnac环境。
展示目标:选手携带自己的攻击机上台,接入靶机所在网段,选手运行exp攻击服务器,若在规定时间内修改密码并登录
https://192.168.143.19:8443/mc2/faces/adminlogin.xhtml即为挑战成功。
ire
题目信息:
题目名称:ire
旗帜名称:IRE
题目描述:附件中给出了一台Ubunt64-bit 22.04.5 LTS虚拟机,环境和展示区相同但密码不同。虚拟机/home/game目录中有start.sh脚本,选手可以执行start.sh脚本启动题目环境(提供的虚拟机中已经通过服务启动)。请挖掘并利用相关程序的漏洞,实现任意命令执行,若靶机弹出计算器则挑战成功。
附件信息:虚拟机用户名和口令为game/game
台上拓扑:交换机同时连接选手攻击机和靶机。靶机中使用vmware(最新版)启动附件中的Ubunt64-bit 22.04.5 LTS环境,并以game用户登录。
展示目标:选手携带自己的攻击机上台,接入靶机所在网段开始进行脆弱性检测,若在规定时间内靶机弹出计算器,即为挑战成功。
ltp
题目信息:
题目名称:ltp
旗帜名称:LTP
题目描述:附件中给出了一台Ubuntu22.04虚拟机,虚拟机上启动了目标lighttp服务,题目文件、配置信息等在附件中也有给出。请针对目标http服务进行漏洞利用,获取qwb用户权限(修改lighttpd主页)。
附件信息:虚拟机密码为qwb@123456。
台上拓扑:交换机同时连接选手攻击机和靶机。靶机中使用vmware(最新版)启动附件中的Ubuntu22.04环境,并以qwb用户登录。
展示目标:选手携带自己的攻击机上台,接入靶机所在网段。操作员以qwb用户登录Ubuntu22.04,测试网络连通性后,选手执行exp,修改主页(位于/var/index.html)成功,即为挑战成功。
OML
题目信息:
题目名称:ohMyLicense
旗帜名称:OML
题目描述:附件中给出了一台Windows Server 2025虚拟机,请针对目标虚拟机挖掘出未授权远程代码执行漏洞并进行利用,获取C:\Users\Public\flag.txt中的内容。
附件信息:附件为台上相同的攻击环境,但是密码不同。附件中Administrator用户对应密码为gV9!mD1{hE。
台上拓扑:交换机同时连接选手攻击机和靶机。靶机中使用vmware(最新版)启动附件中的Windows Server 2025环境。
展示目标:选手携带自己的攻击机上台,接入靶机所在网段,选手运行exp攻击Windows Server 2025服务器,若在规定时间内获取C:\Users\Public\flag.txt中的内容,即为挑战成功。
OPDD
题目信息:
题目名称:OPDD
旗帜名称:OPDD
题目描述:附件中给出了一个opnsense的虚拟机。初始化过程中set up VLANS 选no,WAN选em0即可。环境和展示区相同但密码不同。请分析并挖掘利用opnsense服务程序的漏洞,实现RCE,并替换修改虚拟机中的/usr/local/www/index.php文件,从而将opnsense的登录页面修改为特定主页。
附件信息:附件为台上相同的环境,但是密码不同。附件中虚拟机系统账密为root/opnsense
台上拓扑:交换机同时连接选手攻击机和靶机。靶机中使用vmware(最新版)开启附件中的虚拟机环境(密码和附件不同),该虚拟机中部署了opnsense。
展示目标:选手携带自己的攻击机上台,需要在规定的时间内攻击web端口的服务程序,实现修改虚拟机中的/usr/local/www/index.php文件,从而将opnsense的登录界面修改为特定页面。需要修改的特定页面详见附件中的index.php,选手展示时需将其中的“XXXXX”替换为自己的队伍名。
rac
题目信息:
题目名称:realAC
旗帜名称:rAC
题目描述:附件中给出了一个虚拟机,环境和展示区相同但密码不同。请实现root权限的RCE,并将展示页面的https://ip:443/login.html修改为特定主页。
附件信息:附件为台上相同的攻击环境(仅密码不同)。
台上拓扑:交换机同时连接选手攻击机和代理虚拟机,代理虚拟机与靶机相连。代理虚拟机将靶机的80,85,443,9998端口,通过端口转发的方式可被选手访问。其中代理虚拟机仅提供端口转发功能。展示目标:选手携带自己的攻击机上台,接入代理虚拟机所在网段,需要在规定的时间内攻击靶机,将https://ip:443/login.html修改为特定页面。需要修改的特定页面详见附件中的login.html,选手展示时需将其中的“XXXXX”替换为自己的队伍名。
ts++
题目信息:
题目名称:thinkshop++
旗帜名称:TS++
题目描述:附件中给出了一个docker虚拟机(名称为thinkshopplus),虚拟机上部署了一个服务系统,请分析服务存在的漏洞,针对Web服务进行攻击,获取操作系统控制权限。并替换修改虚拟机中的/var/www/html/public/hack.html文件,从而将http://ip:port/public/hack.html的页面修改为特定页面。
附件信息:附件为台上相同的攻击环境。Web服务内部暴露端口为80,部署方式:
docker load < thinkshopplus.tar
docker run -tid –name thinkshopplus -p 36000:80 thinkshopplus
台上拓扑:交换机同时连接选手攻击机和靶机。靶机运行docker虚拟机启动Web服务,并将内部80端口映射到指定端口。
展示目标:选手携带自己的攻击机上台,接入靶机所在网段,需要在规定的时间内攻击指定端口的Web服务,实现RCE,并替换修改虚拟机中的/var/www/html/public/hack.html文件,从而将http://ip:port/public/hack.html的页面修改为附件中所提供的hack.html,其中选手展示时需将其中的“XXX”替换为自己的队伍名。
Ubp
题目信息:
题目名称:UbuntuPrv
旗帜名称:UbP
题目描述:附件中以OVF格式给出了一个VMWare17.5以上兼容性的Ubuntu虚拟机,Ubuntu虚拟机的内核经过修改重新编译,请利用漏洞提升至root权限。导入后的宿主机有一调试用户。调试用户的用户名为qwbs8,密码为8f4cpkdjwN2YPPra;
台上拓扑:交换机同时连接选手攻击机和靶机。靶机中使用vmware(最新版)开启附件中的Ubuntu虚拟机环境,虚拟机在22号端口开启ssh访问,映射到宿主机的11122端口,可以在攻击机通过scp协议将exp传输到虚拟机进行攻击。展示机包含调试用户,但是密码不同,无法通过ssh访问。选手通过操作账号连接ssh。操作账号的用户名为qwbs8_user,密码为123456。
展示目标:选手携带自己的攻击机上台,可以通过ssh直接登录客户虚拟机,上传文件并执行操作。选手需要在规定的时间内攻击虚拟机,得到root权限,并能够读取/etc/shadow文件。
WPNet
题目信息:
题目名称:WPNet
旗帜名称:WPNet
题目描述:附件中给出了一台Windows 10 x64虚拟机,及一台Ubuntu虚拟机,两台虚拟机均使用桥接模式,网段配置为:192.168.3.0。Windows虚拟机中安装有WPS应用程序,选手可上传1个doc或docx文件,并使用WPS打开;在攻击环境中,Ubuntu与Windows虚拟机处于同一局域网内,并开启了Apache服务。请选手针对Windows虚拟机上的wps进行漏洞利用,实现RCE(弹出计算器)。
附件信息:附件为台上相同的攻击环境。附件中Windows用户未设置密码,Ubuntu中qwb用户密码为welcometoqwb。
台上拓扑:交换机同时连接选手攻击机和靶机。靶机中使用vmware启动附件中的Windows 10环境。
展示目标:选手携带自己的攻击机上台,接入靶机所在网段,并开启http服务(如python3 -m http.server)。操作员登录Windows,下载选手使用的exp.doc或exp.docx,并使用WPS打开exp文件(展示期间可多次执行),若在规定时间内靶机弹出calc计算器,即为挑战成功。
Thinking
4号下午到酒店之后,大概4点去场馆溜了一圈,大门如图
比赛的地方在4楼赛博厅
当时工作人员还在测试,我们就走进去看了一圈。两边是32支战队的战队logo,口号以及战队简介,一边各16支战队
5号上午比赛正式开始的时候,场地中间插满了旗子,真就夺旗赛,但这些特殊的旗都是RW相关的赛题,一血的队伍就可以把旗子拔走
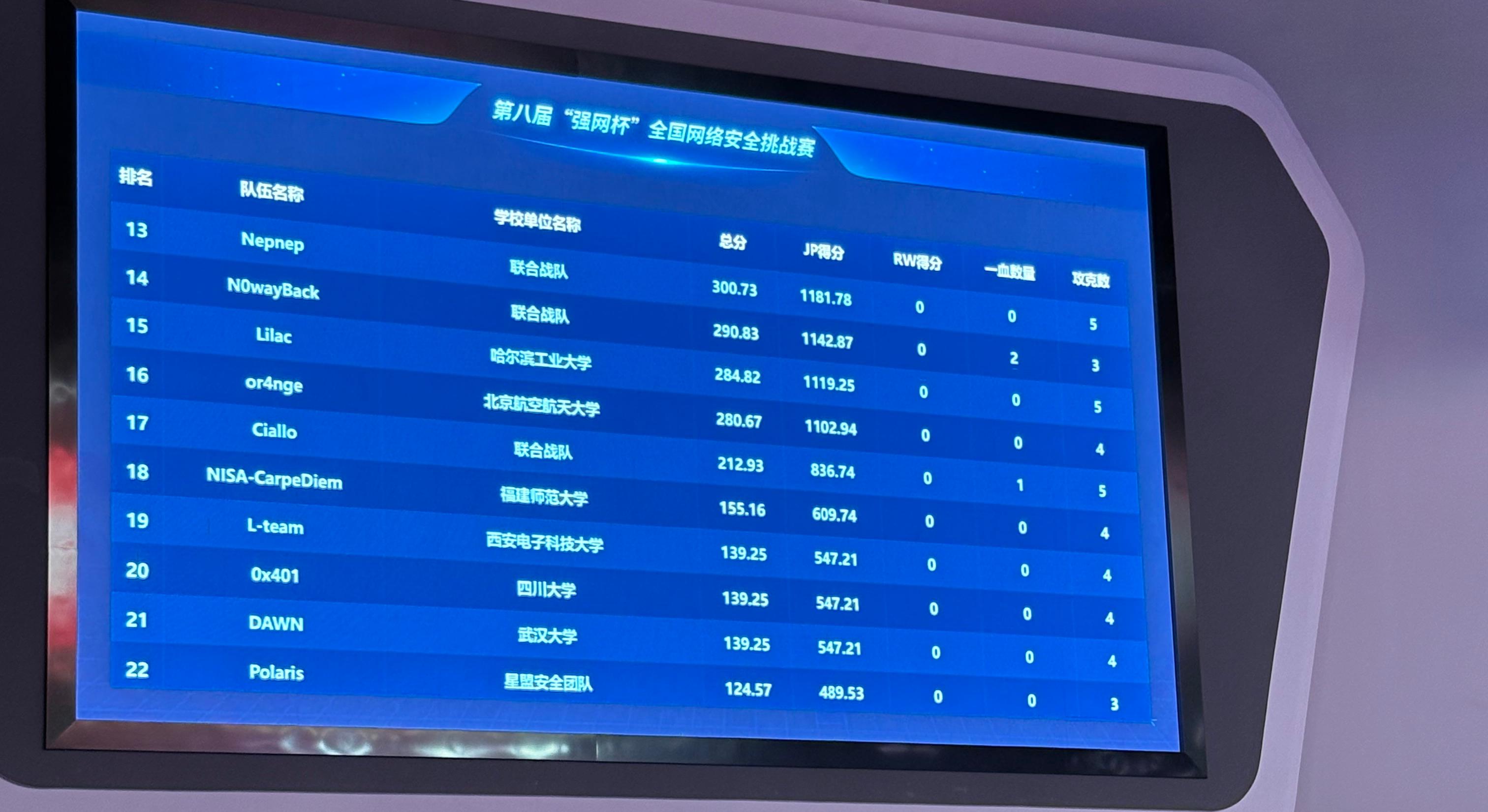
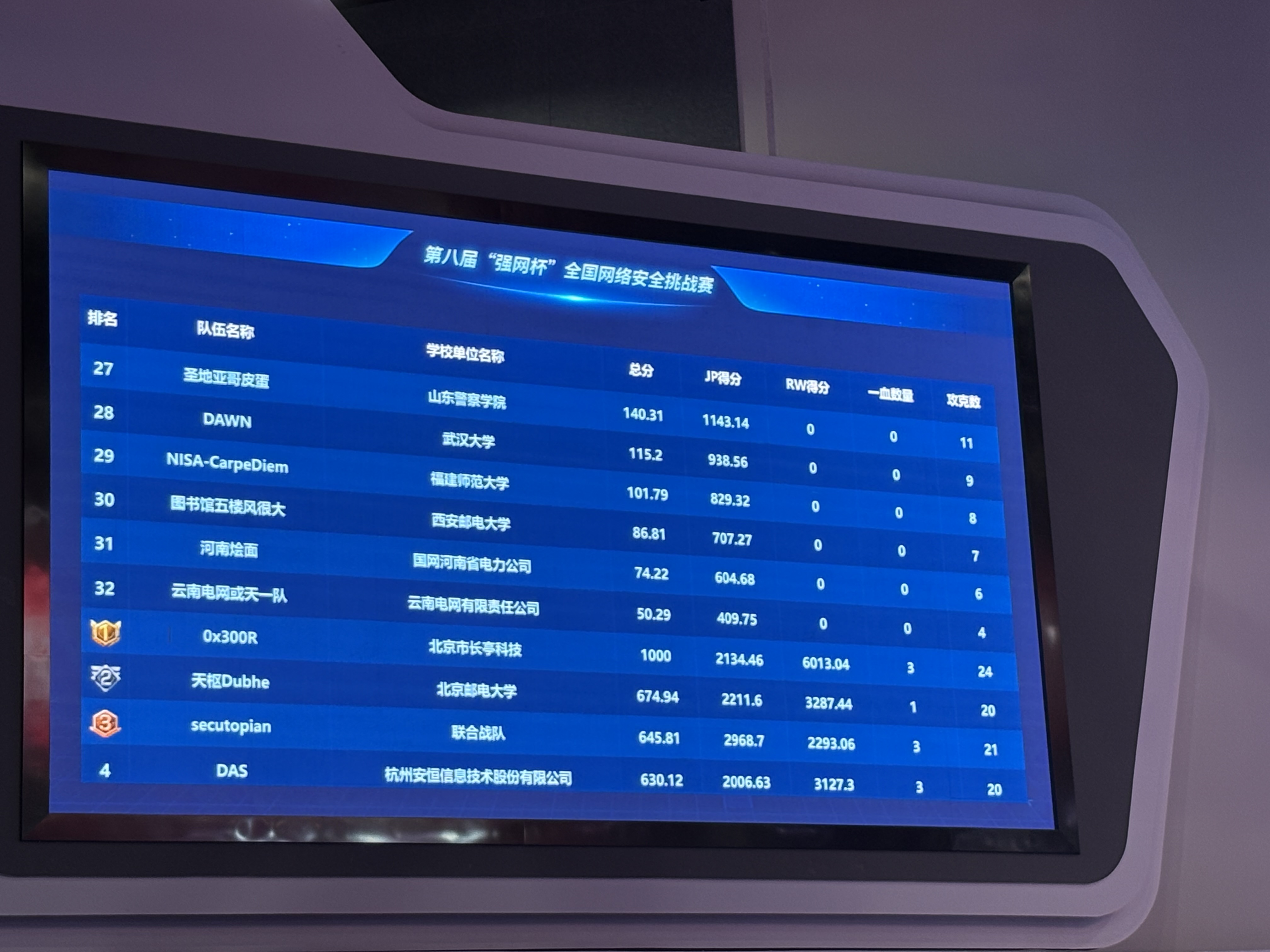
接着讲讲我这一天干了啥,早上做了下Shopping game,手还算快,第八个做出来,然后去看st,逆了半天没触碰到一点密码的东西就放弃了,然后队友那边有个关于FXPDF的payload,让我试了试,题目要求的功能是实现了,但是很可惜,有多余的操作,所以上台挑战的时候没给过。到了下午2点放新题,我一看,好家伙上了3道密码,这让我怀疑这是强网杯还是强密杯。啃了两个多小时还好把bl0ck做了出来(也还算挺靠前的,好像也是第八个做了出来),到5点比赛结束最终排名定格在17名(Jeopardy部分),总榜不太确定,最后主办方连榜单都没放。说实话是远超预期,昨天和队友看了各大战队之后实在是想不到我们这双非战队能稳赢哪支队伍,一来我们4个实力就一般,二来比赛可联网,大家肯定都有后备力量,而我们….一言难尽,比啥都比不过😭
噢,最后我们快走的时候还被拉去拍了点照片和视频当作宣传
接下来是6号的事情。
早上刚开赛,和我预期的差不多,大部分队伍都把前一天的题目做完了,而我们依旧没有进展,自然而然掉到了末尾。10点上了最后两题密码(Signin和f2ke),可惜没做出来。
花了挺长时间把fak1做了出来,然后就摆烂等颁奖了。心有余而力不足,只能做出一些大家都会做的题,最后定榜29名😭
晚上吃完饭后和星盟的师傅去ktv玩了一会儿,还挺开心的😀。
最后感谢一下主办方吧,谁叫强网杯给的这么多呢。定制队伍的赛牌(还区分了队长和队员),有车费报销,有酒店,给了背包和鼠标垫周边,还保底3等奖(喜提1w)。但线下赛有点像不需要交wp的ISCC(这是能说的吗?)
事已至此,我的CTF生涯就暂且告一段落了!!!!!!